News outlets are once again calling for hacking of elections, this time the targeted elections are those of France. It is funny that most of the outlets reporting on this, like Politico are publishing with tiny letters as an "opinion" piece. Everything these days is an opinion piece in which everyone just throws mud and they hope it sticks. From a cyber security perspective with the current system in the United States which was also allegedly "hacked" by the Russians according to the media, someone has to call BS on these stories. Many districts are paper based, voting machines are not connected to the internet or connected to each-other, and so on.
Now we go again with the same idiots who are calling for "everything is hacked" mentality. What media is mixing up is hacking and information warfare. Silly when you think about it since they have been waging a information warfare against their own citizens for some time now. I had the privilege of taking the information warfare class during the elections in the United States and you could not find better time to do it. You can follow step by step instructions from the textbook and see them in the media propaganda machine. People have become so brainwashed and delusional that they believe whatever the media serves them up. This goes for all parties involved, left and right. Media is nothing but a propaganda machine that serves the interest of their shareholders which are super rich, career politicians that give them access, and special interests that sponsor them and pay for their add's.
What upsets me the most is that uneducated people who don't understand how "hacking" or networking or anything else related to computing works, and run for their pitchforks the moment they hear it in the news. People have been discussing Hillary's e-mail for so long, but no-one mentioned that a 10 year old could have hacked it the way it was set up. When you send thousands of e-mails a day its easy to compromise someone else inside your circle and get the server IP from an e-mail header. From there it just takes enumerating, testing for vulnerabilities and waiting. Or if you are lazy spear phishing e-mail from one of the inner circle people can do the job done. Voting machines however don't send out e-mails to their friends, don't connect to the internet, don't download torrents, and don't click on phishing e-mails.
Don't fall for the media war drums which if left unchecked could drives us into a World War III. Sensationalism sells and if there was no bickering between political parties who would ever read their "opinions" and "editorials". Real journalism has died with the invention of the internet and the speed with which consumers expect to consume new information. If you want to remember what journalism looks like read something like National Geographic article where they spend months and years researching a specific topic.
Good night. :)
Sunday, April 23, 2017
Sunday, April 16, 2017
Week 5 Blog Post
This week I would like to discuss the need for more cyber security professionals in the US. There are several reasons why, some of them being outside threats, state sponsored hacking groups, plain criminals, and need for securing our domestic infrastructure. Every day we have news about new US companies being hacked to just few days ago someone hacking the emergency sirens in Dallas.
So why don't we just get more cyber security professionals. Well here are some of my observations. The entry into the career of a cyber security professional is extremely difficult. To get a job in the private or government sector one has to have several years of hand on experience. Most businesses require a certification such as CISSP or similar which have prerequisites of being in the field and having several years of experience in order to get certified. How is one going to get the experience when every single job posting requires certifications and experience which a student doesn't have.
The next problem I personally have is the transition into the security career. I have worked with data and analytics for 15 years and as a Manager in my current job, I would have to drop into a entry role that doesn't require a security certification (which they all do). I would have to start at half of what I earn now while having a Master's degree in cyber security. What is the incentive for us wanting to work in this industry. The median pay of 66k annually? That is one sad pay rate for someone who has to learn about thousands of different things such as networking, encryption, cloud computing, risk management, operating systems and so on. The amount of learning and skill does not translate into the pay scale of a security professional. Compare that to a data scientist who can earn six figures with much less skill, learning and no certification required straight out of college. For what? Few statistics models, knowing a bit of "R" and building few queries in SAS during their education. While we are expected to be experts in everything in order to protect assets against most cunning black hat's, criminal organisations, and terrorists. It just doesn't add up.
What do you think?
This is the end of my rant and my blog post for this week.
So why don't we just get more cyber security professionals. Well here are some of my observations. The entry into the career of a cyber security professional is extremely difficult. To get a job in the private or government sector one has to have several years of hand on experience. Most businesses require a certification such as CISSP or similar which have prerequisites of being in the field and having several years of experience in order to get certified. How is one going to get the experience when every single job posting requires certifications and experience which a student doesn't have.
The next problem I personally have is the transition into the security career. I have worked with data and analytics for 15 years and as a Manager in my current job, I would have to drop into a entry role that doesn't require a security certification (which they all do). I would have to start at half of what I earn now while having a Master's degree in cyber security. What is the incentive for us wanting to work in this industry. The median pay of 66k annually? That is one sad pay rate for someone who has to learn about thousands of different things such as networking, encryption, cloud computing, risk management, operating systems and so on. The amount of learning and skill does not translate into the pay scale of a security professional. Compare that to a data scientist who can earn six figures with much less skill, learning and no certification required straight out of college. For what? Few statistics models, knowing a bit of "R" and building few queries in SAS during their education. While we are expected to be experts in everything in order to protect assets against most cunning black hat's, criminal organisations, and terrorists. It just doesn't add up.
What do you think?
This is the end of my rant and my blog post for this week.
Sunday, April 9, 2017
Defcon 2017 - here we come
This may not be the general class topic but I wanted to share some awesome news - we are heading out to Defcon this summer. And did I mention its for free :)
My wife works for a large University and she gets to go to certain medical conventions. As I am graduating next semester we were planning to go to Defcon as my graduation present. Well thanks to the Biohacking Village we were able to tie Defcon as an eligible conference which is tied to medical field, and have the whole trip paid by the University.
What is the Biohacking Village?
In their own words:
"The DEF CON Biohacking Village is a multi-day biotechnology conference focused on breakthrough DIY, grinder, transhumanist, medical technology, and information security along with its related communities in the open source ecosystem."
This may not be the general class topic but I wanted to share some awesome news - we are heading out to Defcon this summer. And did I mention its for free :)
My wife works for a large University and she gets to go to certain medical conventions. As I am graduating next semester we were planning to go to Defcon as my graduation present. Well thanks to the Biohacking Village we were able to tie Defcon as an eligible conference which is tied to medical field, and have the whole trip paid by the University.
What is the Biohacking Village?
In their own words:
"The DEF CON Biohacking Village is a multi-day biotechnology conference focused on breakthrough DIY, grinder, transhumanist, medical technology, and information security along with its related communities in the open source ecosystem."
I am actually very excited to learn more about Biohacking as I have covered some of the risks in one of my previous classes. My interest is in medical device hacking but to be honest I could enjoy just about any topic related to hacking. The list of presenters and topics is still being put together so I cant provide more detialed information but here is the official site for everyone who is interested.
https://www.defconbiohackingvillage.org/
I hope I will see some of my classmates or professors at this years Defcon.
See you there....
Sunday, April 2, 2017
New Ransom demand for iCloud Credentials
Some time ago cloud discussions were a scary topic for me. It felt so distant and complex that I didn't believe I could ever get my head around such a topic. Eventually I decided to take an elective class on Cloud Computing and all my fears went away. It got to the point where I always get excited to talk to others at work about different deployment models and service models that cloud offers.
In the Cloud Computing class we have covered many aspects of cloud security and analysed the increased growth of the industry. Some experts have predicted a 95% share of Cloud Computing for organizations within a next one to two decades. While this is great news, for me it has also become something that made me uneasy. One thing that always comes to mind is that we have few cloud giants that are holding too much data from various industries. To big to fail concept anyone? As these giants grow they are creating an unique new risk. What happens when these mega providers get attacked or shut down. Many companies who rely on software or platform as a service would not be able to conduct their day to day business. We entrust these providers with our personal and our business data with the expectation of high availability and minimum downtime. this is why the ransom of Apple's iCloud hits home with me.
As reported in the article by David Jones on March 24th 2017, Apple has received a ransom threat from a hacking group claiming to have access to data for up to 800 Million iCloud accounts. Hackers are threatening to reset passwords and wipe all information including wiping the iPhones of iCloud users unless paid $700k. - http://www.technewsworld.com/story/84406.html
As mentioned before as the cloud providers continue to grow the risk of attacks on concentrated data centers and applications will continue to grow. Do you think that centralizing such vast amounts of information confined to few mega providers is a smart solution, in times of cyber terrorism and state sponsored hacking groups?
VULNERABILITIES
During this week we are going to review few credible sources for vulnerabilities you should know about. For me generally the starting point for any vulnerability research starts with Common Vulnerabilities and Exposures (CVE) site.
1.) Common Vulnerabilities and Exposures Website
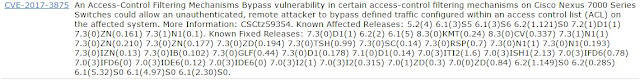
CVE is sponsored by the US-CERT in the office of Cyber-security and Communications at the U.S. Department of Homeland Security. It contains searchable database of all published vulnerabilities and makes it easy to check them for an asset or software. the address is https://cve.mitre.org/
Here is an example of the search result:
2.) Computer Security Resource Center (NIST)
The National Institute of Standards and Technology (NIST) is first stop for anyone who is in the field of IT Security or Risk Management. Information contained on this site includes numerous publications on variety of topics including guidelines and instruction on how to complete different task related to the topics. In addition many templates and frameworks are included which are used in Federal government applications and can be easily transitioned into most private sector organisations. Link to the site is https://nvd.nist.gov
Here is the example of the same vulnerability including risk ranking, mitigation techniques and many other valuable details a Cyber security professional should know.
There are many other sites that offer information related to vulnerabilities but for me these two are the primary ones to review when doing risk assessment or threat modeling.
Subscribe to:
Comments (Atom)