When looking at hackers we often see the image of criminals stealing information and selling it on the underground market or some foreign criminals. But that is not the full story. Today we see hackers that fall into three major categories. Black hats or the criminal elements listed above. Grey hats which walk the line between criminal and legitimate and white hats that are essentially the good guys of the three.
As technological demand for security experts grows some of the black and grey hats are taking the plunge into becoming white hats. The financial incentives and no risk make this a great choice for many former criminal hackers. Some countries like Romania in Europe have so many hackers that they have turned into legitimate business enterprises that it produces up to 6% of the whole country's gross domestic product.
Companies are proactively looking for some of these former criminals because of their security knowledge. The skills they bring to the table help companies harden their security or they can provide services to the intelligence communities for which they may not have the right staff to do it. Security consulting businesses are growing at a mind boggling rates. Some of them are even being employed as a cyber defense shield against military cyber attacks on other nations. I expect to see this trend develop further in the future as the global IOT market grows and the need for cyber security experts reaches critical levels.
Saturday, June 3, 2017
Sunday, May 21, 2017
Week 10 Blog Post
In week 9-10 we have created an "Action Plan" for our Harry & Mae Company. For some of you who have not encountered the Harry and Mae case study, the case is about a fictions company that is franchising restaurants across the US. You are given video presentations about the company, company assets, policies and procedures which you analyse for different classes you take.
This time the assignment was to create an action plan to resolve all physical and asset vulnerabilities and harden the business after a credit card breach. As of right now my paper is about 23 pages long and covers asset identification, asset vulnerability assessments, policy and procedure review, glossary of terms used, network diagram, threat model and the action plan to resolve and mitigate vulnerabilities.
Most fun part about the assignment was to research all the vulnerabilities associated with the assets. Example of this is below.
After the vulnerabilities were listed (lets just say there were many) the next step was to find ways to mitigate them. This was done by assigning a control to the process and addressing the vulnerability itself. Most mitigation techniques were collected from CVE MITRE.
Overall a very good assignment where students learn first hand how to find and address vulnerabilities and conduct risk assessments.
This time the assignment was to create an action plan to resolve all physical and asset vulnerabilities and harden the business after a credit card breach. As of right now my paper is about 23 pages long and covers asset identification, asset vulnerability assessments, policy and procedure review, glossary of terms used, network diagram, threat model and the action plan to resolve and mitigate vulnerabilities.
Most fun part about the assignment was to research all the vulnerabilities associated with the assets. Example of this is below.
After the vulnerabilities were listed (lets just say there were many) the next step was to find ways to mitigate them. This was done by assigning a control to the process and addressing the vulnerability itself. Most mitigation techniques were collected from CVE MITRE.
Overall a very good assignment where students learn first hand how to find and address vulnerabilities and conduct risk assessments.
Sunday, May 14, 2017
Week 9 Blog Post
As many of you have seen in the news over the last few days a massive global ransomware attack has hit hundreds of thousands of organisations in over 150 countries. The attack was first noticed on Friday as the ransomware started propagating in a very unusual way, via worm.
So far according to the news outlets the worm was accidentally stopped when a security researcher registered the domain that was referenced in the worm code. Apparently this was the built in kill switch for the worm.
The gizmodo website contains a video showing the malware infecting a system which then continues to infect the other system in real time.
Here is the link. Malware infection Video
Even though the worm has infected many organisations world wide the money collected from victims as of yesterday was only about $33k. There is still some concern about all the additional computers that are infected, because the companies wont know until Monday when they start them up.
Some security experts are also warning that since the developers now know how the worm was stopped they may change the kill switch and release a new version.
Be on the lookout and patch your systems.
So far according to the news outlets the worm was accidentally stopped when a security researcher registered the domain that was referenced in the worm code. Apparently this was the built in kill switch for the worm.
The gizmodo website contains a video showing the malware infecting a system which then continues to infect the other system in real time.
Here is the link. Malware infection Video
Even though the worm has infected many organisations world wide the money collected from victims as of yesterday was only about $33k. There is still some concern about all the additional computers that are infected, because the companies wont know until Monday when they start them up.
Some security experts are also warning that since the developers now know how the worm was stopped they may change the kill switch and release a new version.
Be on the lookout and patch your systems.
Sunday, May 7, 2017
Week 8 Blog Post
In these last few weeks of this semester we are looking at different Cybersecurity trends for 2017. There is not much change from existing trends to be expected, unless we see some black swan effect attack that no one has ever anticipated. The trends continue to evolve around your standard malware distribution, ransomware, IOT hacking, DDoS attacks, cloud attacks, data breaches, spear phishing, mobile device security and other familiar trends.
These trends generally follow the growth in the specific market such as cloud computing or Internet of Things (IOT) growth. As more and more devices are built with capability to connect to the internet, and are built with insufficient security in mind they could and will end up getting hacked and used for other purposes. Most recent example of the Dyn attack caused by Mira botnet is a testimony to that growing trend. In this case infected IOT devices were turned into a large botnet used to bring down business and media outlet websites. The DDoS and ransomware attacks have been around for a while but will continue through 2017 as there are no real mitigation techniques to deal with such attacks on a large scale. Data breaches continue to stay in the news and will do so in 2017 as well. I personally think this is due to lack of penalties for the businesses that suffer a data breach. Currently the fines are to low and consumers only benefit they get is a free one year credit monitoring joke for their lost data. It's like consumer information experises after 12 months and becomes useless to the attackers. The SSN doesn't change, your DOB doesn't change, your mother's maiden name doesn't change so why would this information become irrelevant after a year? We need more strict penalties including cease and decist orders for companies with large data breaches. When they get scared they tend to invest more into security and pay more attention. When all they have to loose is few million dollars and bulk purchase of credit monitoring then no-one really cares that much. Mobile devices will most likely start getting hit at much larger scale with ransomware attacks as they collect more and more information on a daily basis. Mobile devices are replacing personal computers and are becoming more attractive targets with app distribution. Also lets not forget that many businesses allow for "BYOD" bring your own device to work which can also allow attackers to target businesses though the personal devices employees bring to work.
In summary we will not see a drop in different attack types this year but can expect an increase. We are also most likely to see an increase in state sponsored attacks as tensions rise between North Korea and the United States. Another emerging segment which will spill over onto cyber conflict is the rise of social movements such as antifa across the globe. This group will start emerging in the realm of cyber terrorism as more right leaning governments are elected and Europe continues to see a split between their members.
In these last few weeks of this semester we are looking at different Cybersecurity trends for 2017. There is not much change from existing trends to be expected, unless we see some black swan effect attack that no one has ever anticipated. The trends continue to evolve around your standard malware distribution, ransomware, IOT hacking, DDoS attacks, cloud attacks, data breaches, spear phishing, mobile device security and other familiar trends.
These trends generally follow the growth in the specific market such as cloud computing or Internet of Things (IOT) growth. As more and more devices are built with capability to connect to the internet, and are built with insufficient security in mind they could and will end up getting hacked and used for other purposes. Most recent example of the Dyn attack caused by Mira botnet is a testimony to that growing trend. In this case infected IOT devices were turned into a large botnet used to bring down business and media outlet websites. The DDoS and ransomware attacks have been around for a while but will continue through 2017 as there are no real mitigation techniques to deal with such attacks on a large scale. Data breaches continue to stay in the news and will do so in 2017 as well. I personally think this is due to lack of penalties for the businesses that suffer a data breach. Currently the fines are to low and consumers only benefit they get is a free one year credit monitoring joke for their lost data. It's like consumer information experises after 12 months and becomes useless to the attackers. The SSN doesn't change, your DOB doesn't change, your mother's maiden name doesn't change so why would this information become irrelevant after a year? We need more strict penalties including cease and decist orders for companies with large data breaches. When they get scared they tend to invest more into security and pay more attention. When all they have to loose is few million dollars and bulk purchase of credit monitoring then no-one really cares that much. Mobile devices will most likely start getting hit at much larger scale with ransomware attacks as they collect more and more information on a daily basis. Mobile devices are replacing personal computers and are becoming more attractive targets with app distribution. Also lets not forget that many businesses allow for "BYOD" bring your own device to work which can also allow attackers to target businesses though the personal devices employees bring to work.
In summary we will not see a drop in different attack types this year but can expect an increase. We are also most likely to see an increase in state sponsored attacks as tensions rise between North Korea and the United States. Another emerging segment which will spill over onto cyber conflict is the rise of social movements such as antifa across the globe. This group will start emerging in the realm of cyber terrorism as more right leaning governments are elected and Europe continues to see a split between their members.
Tuesday, May 2, 2017
Week 7 Blog Post - Is the Impact of Power Grid Hacking Exaturated?
In one of my classes this past week a discussion topic of severity of power grid hacking/attack came under debate. What makes this topic so interesting is also that it appears in the news all the time and in politics. So the article by Washington Post from January named "Russian hackers penetrated U.S. electricity grid through a utility in Vermont, U.S. officials say." must make you scared. Don't worry friends, I will not discuss politics this week, and the article was debunked as fake anyways.
What I wanted to share is that based on all the research I have done, the impact of power grid outages is in vast majority of cases are only short lived. This means even the most devastating power grid blackouts in U.S. history have been resolved in less then a day. The only outages that lasted longer then one to two days are tied to natural disasters such as hurricanes that have caused such damage. From the empirical and a risk perspective I cannot back up the hysteria with evidence, that a hacker caused event could trigger a long lasting power grid outage that could bring the U.S. economy down.
As I said to one of my fellow classmates if anything a brief power outage would do good for the economy. While most businesses can write off any income loss from their taxes the real benefit would be in the sale of goods to recover loss of spoiled food, generators during outage, fuel, wood, batteries and so forth. I guess you can just look at goods being sold before major hurricane strike and you should be able to predict the economic growth. I also did look at historical stock data and compared it to the dates of each of the major U.S. power grid outages and I have not seen a specific dip indicating a long term effect of any kind on the economy, as some people have claimed.
Anyways please let me know what you think?
What I wanted to share is that based on all the research I have done, the impact of power grid outages is in vast majority of cases are only short lived. This means even the most devastating power grid blackouts in U.S. history have been resolved in less then a day. The only outages that lasted longer then one to two days are tied to natural disasters such as hurricanes that have caused such damage. From the empirical and a risk perspective I cannot back up the hysteria with evidence, that a hacker caused event could trigger a long lasting power grid outage that could bring the U.S. economy down.
As I said to one of my fellow classmates if anything a brief power outage would do good for the economy. While most businesses can write off any income loss from their taxes the real benefit would be in the sale of goods to recover loss of spoiled food, generators during outage, fuel, wood, batteries and so forth. I guess you can just look at goods being sold before major hurricane strike and you should be able to predict the economic growth. I also did look at historical stock data and compared it to the dates of each of the major U.S. power grid outages and I have not seen a specific dip indicating a long term effect of any kind on the economy, as some people have claimed.
Anyways please let me know what you think?
Sunday, April 23, 2017
New Election "Hacking" War Drums Are Getting Boring - Week 6 Blog Post
News outlets are once again calling for hacking of elections, this time the targeted elections are those of France. It is funny that most of the outlets reporting on this, like Politico are publishing with tiny letters as an "opinion" piece. Everything these days is an opinion piece in which everyone just throws mud and they hope it sticks. From a cyber security perspective with the current system in the United States which was also allegedly "hacked" by the Russians according to the media, someone has to call BS on these stories. Many districts are paper based, voting machines are not connected to the internet or connected to each-other, and so on.
Now we go again with the same idiots who are calling for "everything is hacked" mentality. What media is mixing up is hacking and information warfare. Silly when you think about it since they have been waging a information warfare against their own citizens for some time now. I had the privilege of taking the information warfare class during the elections in the United States and you could not find better time to do it. You can follow step by step instructions from the textbook and see them in the media propaganda machine. People have become so brainwashed and delusional that they believe whatever the media serves them up. This goes for all parties involved, left and right. Media is nothing but a propaganda machine that serves the interest of their shareholders which are super rich, career politicians that give them access, and special interests that sponsor them and pay for their add's.
What upsets me the most is that uneducated people who don't understand how "hacking" or networking or anything else related to computing works, and run for their pitchforks the moment they hear it in the news. People have been discussing Hillary's e-mail for so long, but no-one mentioned that a 10 year old could have hacked it the way it was set up. When you send thousands of e-mails a day its easy to compromise someone else inside your circle and get the server IP from an e-mail header. From there it just takes enumerating, testing for vulnerabilities and waiting. Or if you are lazy spear phishing e-mail from one of the inner circle people can do the job done. Voting machines however don't send out e-mails to their friends, don't connect to the internet, don't download torrents, and don't click on phishing e-mails.
Don't fall for the media war drums which if left unchecked could drives us into a World War III. Sensationalism sells and if there was no bickering between political parties who would ever read their "opinions" and "editorials". Real journalism has died with the invention of the internet and the speed with which consumers expect to consume new information. If you want to remember what journalism looks like read something like National Geographic article where they spend months and years researching a specific topic.
Good night. :)
Now we go again with the same idiots who are calling for "everything is hacked" mentality. What media is mixing up is hacking and information warfare. Silly when you think about it since they have been waging a information warfare against their own citizens for some time now. I had the privilege of taking the information warfare class during the elections in the United States and you could not find better time to do it. You can follow step by step instructions from the textbook and see them in the media propaganda machine. People have become so brainwashed and delusional that they believe whatever the media serves them up. This goes for all parties involved, left and right. Media is nothing but a propaganda machine that serves the interest of their shareholders which are super rich, career politicians that give them access, and special interests that sponsor them and pay for their add's.
What upsets me the most is that uneducated people who don't understand how "hacking" or networking or anything else related to computing works, and run for their pitchforks the moment they hear it in the news. People have been discussing Hillary's e-mail for so long, but no-one mentioned that a 10 year old could have hacked it the way it was set up. When you send thousands of e-mails a day its easy to compromise someone else inside your circle and get the server IP from an e-mail header. From there it just takes enumerating, testing for vulnerabilities and waiting. Or if you are lazy spear phishing e-mail from one of the inner circle people can do the job done. Voting machines however don't send out e-mails to their friends, don't connect to the internet, don't download torrents, and don't click on phishing e-mails.
Don't fall for the media war drums which if left unchecked could drives us into a World War III. Sensationalism sells and if there was no bickering between political parties who would ever read their "opinions" and "editorials". Real journalism has died with the invention of the internet and the speed with which consumers expect to consume new information. If you want to remember what journalism looks like read something like National Geographic article where they spend months and years researching a specific topic.
Good night. :)
Sunday, April 16, 2017
Week 5 Blog Post
This week I would like to discuss the need for more cyber security professionals in the US. There are several reasons why, some of them being outside threats, state sponsored hacking groups, plain criminals, and need for securing our domestic infrastructure. Every day we have news about new US companies being hacked to just few days ago someone hacking the emergency sirens in Dallas.
So why don't we just get more cyber security professionals. Well here are some of my observations. The entry into the career of a cyber security professional is extremely difficult. To get a job in the private or government sector one has to have several years of hand on experience. Most businesses require a certification such as CISSP or similar which have prerequisites of being in the field and having several years of experience in order to get certified. How is one going to get the experience when every single job posting requires certifications and experience which a student doesn't have.
The next problem I personally have is the transition into the security career. I have worked with data and analytics for 15 years and as a Manager in my current job, I would have to drop into a entry role that doesn't require a security certification (which they all do). I would have to start at half of what I earn now while having a Master's degree in cyber security. What is the incentive for us wanting to work in this industry. The median pay of 66k annually? That is one sad pay rate for someone who has to learn about thousands of different things such as networking, encryption, cloud computing, risk management, operating systems and so on. The amount of learning and skill does not translate into the pay scale of a security professional. Compare that to a data scientist who can earn six figures with much less skill, learning and no certification required straight out of college. For what? Few statistics models, knowing a bit of "R" and building few queries in SAS during their education. While we are expected to be experts in everything in order to protect assets against most cunning black hat's, criminal organisations, and terrorists. It just doesn't add up.
What do you think?
This is the end of my rant and my blog post for this week.
So why don't we just get more cyber security professionals. Well here are some of my observations. The entry into the career of a cyber security professional is extremely difficult. To get a job in the private or government sector one has to have several years of hand on experience. Most businesses require a certification such as CISSP or similar which have prerequisites of being in the field and having several years of experience in order to get certified. How is one going to get the experience when every single job posting requires certifications and experience which a student doesn't have.
The next problem I personally have is the transition into the security career. I have worked with data and analytics for 15 years and as a Manager in my current job, I would have to drop into a entry role that doesn't require a security certification (which they all do). I would have to start at half of what I earn now while having a Master's degree in cyber security. What is the incentive for us wanting to work in this industry. The median pay of 66k annually? That is one sad pay rate for someone who has to learn about thousands of different things such as networking, encryption, cloud computing, risk management, operating systems and so on. The amount of learning and skill does not translate into the pay scale of a security professional. Compare that to a data scientist who can earn six figures with much less skill, learning and no certification required straight out of college. For what? Few statistics models, knowing a bit of "R" and building few queries in SAS during their education. While we are expected to be experts in everything in order to protect assets against most cunning black hat's, criminal organisations, and terrorists. It just doesn't add up.
What do you think?
This is the end of my rant and my blog post for this week.
Sunday, April 9, 2017
Defcon 2017 - here we come
This may not be the general class topic but I wanted to share some awesome news - we are heading out to Defcon this summer. And did I mention its for free :)
My wife works for a large University and she gets to go to certain medical conventions. As I am graduating next semester we were planning to go to Defcon as my graduation present. Well thanks to the Biohacking Village we were able to tie Defcon as an eligible conference which is tied to medical field, and have the whole trip paid by the University.
What is the Biohacking Village?
In their own words:
"The DEF CON Biohacking Village is a multi-day biotechnology conference focused on breakthrough DIY, grinder, transhumanist, medical technology, and information security along with its related communities in the open source ecosystem."
This may not be the general class topic but I wanted to share some awesome news - we are heading out to Defcon this summer. And did I mention its for free :)
My wife works for a large University and she gets to go to certain medical conventions. As I am graduating next semester we were planning to go to Defcon as my graduation present. Well thanks to the Biohacking Village we were able to tie Defcon as an eligible conference which is tied to medical field, and have the whole trip paid by the University.
What is the Biohacking Village?
In their own words:
"The DEF CON Biohacking Village is a multi-day biotechnology conference focused on breakthrough DIY, grinder, transhumanist, medical technology, and information security along with its related communities in the open source ecosystem."
I am actually very excited to learn more about Biohacking as I have covered some of the risks in one of my previous classes. My interest is in medical device hacking but to be honest I could enjoy just about any topic related to hacking. The list of presenters and topics is still being put together so I cant provide more detialed information but here is the official site for everyone who is interested.
https://www.defconbiohackingvillage.org/
I hope I will see some of my classmates or professors at this years Defcon.
See you there....
Sunday, April 2, 2017
New Ransom demand for iCloud Credentials
Some time ago cloud discussions were a scary topic for me. It felt so distant and complex that I didn't believe I could ever get my head around such a topic. Eventually I decided to take an elective class on Cloud Computing and all my fears went away. It got to the point where I always get excited to talk to others at work about different deployment models and service models that cloud offers.
In the Cloud Computing class we have covered many aspects of cloud security and analysed the increased growth of the industry. Some experts have predicted a 95% share of Cloud Computing for organizations within a next one to two decades. While this is great news, for me it has also become something that made me uneasy. One thing that always comes to mind is that we have few cloud giants that are holding too much data from various industries. To big to fail concept anyone? As these giants grow they are creating an unique new risk. What happens when these mega providers get attacked or shut down. Many companies who rely on software or platform as a service would not be able to conduct their day to day business. We entrust these providers with our personal and our business data with the expectation of high availability and minimum downtime. this is why the ransom of Apple's iCloud hits home with me.
As reported in the article by David Jones on March 24th 2017, Apple has received a ransom threat from a hacking group claiming to have access to data for up to 800 Million iCloud accounts. Hackers are threatening to reset passwords and wipe all information including wiping the iPhones of iCloud users unless paid $700k. - http://www.technewsworld.com/story/84406.html
As mentioned before as the cloud providers continue to grow the risk of attacks on concentrated data centers and applications will continue to grow. Do you think that centralizing such vast amounts of information confined to few mega providers is a smart solution, in times of cyber terrorism and state sponsored hacking groups?
VULNERABILITIES
During this week we are going to review few credible sources for vulnerabilities you should know about. For me generally the starting point for any vulnerability research starts with Common Vulnerabilities and Exposures (CVE) site.
1.) Common Vulnerabilities and Exposures Website
CVE is sponsored by the US-CERT in the office of Cyber-security and Communications at the U.S. Department of Homeland Security. It contains searchable database of all published vulnerabilities and makes it easy to check them for an asset or software. the address is https://cve.mitre.org/
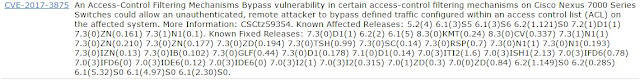
Here is an example of the search result:
2.) Computer Security Resource Center (NIST)
The National Institute of Standards and Technology (NIST) is first stop for anyone who is in the field of IT Security or Risk Management. Information contained on this site includes numerous publications on variety of topics including guidelines and instruction on how to complete different task related to the topics. In addition many templates and frameworks are included which are used in Federal government applications and can be easily transitioned into most private sector organisations. Link to the site is https://nvd.nist.gov
Here is the example of the same vulnerability including risk ranking, mitigation techniques and many other valuable details a Cyber security professional should know.
There are many other sites that offer information related to vulnerabilities but for me these two are the primary ones to review when doing risk assessment or threat modeling.
Wednesday, March 15, 2017
About me:
I am a graduate student at Bellevue University completing my MS Degree in Cybersecurity. I have worked for the last 14 years at a Fortune 50 company in various MIS and IT roles. Currently I am a MIS manager in the banking division.
This blog is part of my capstone class CYBER650 - "Current trends in Cybersecurity."
The CYBER650 class is designed to provide hands on approach to threat modeling for information systems. I will use this blog to write about current cyber security threats and/or developing threat models used to identify threats.
Join me in my final educational chapter of becoming a Cyber security professional.
Subscribe to:
Comments (Atom)